 Ryan Alexander joined Taxpayers for Common Sense as president in 2006, after serving on its board for more than seven years. Founded in 1995, the organization acts as a nonpartisan budget watchdog that serves as an independent voice for American taxpayers. With a grant from our Cyber Initiative, Taxpayers for Common Sense recently produced a Cyber Spending Database to help answer the question of how much the federal government is spending on cyber programs.
Ryan Alexander joined Taxpayers for Common Sense as president in 2006, after serving on its board for more than seven years. Founded in 1995, the organization acts as a nonpartisan budget watchdog that serves as an independent voice for American taxpayers. With a grant from our Cyber Initiative, Taxpayers for Common Sense recently produced a Cyber Spending Database to help answer the question of how much the federal government is spending on cyber programs.
Why did you create the Cyber Spending Database?
At Taxpayers for Common Sense, we track budget proposals and appropriations bills across the federal budget, so we see shifts as they happen, sometimes dramatically, and sometimes subtly. Before we started tracking cyber spending to create the database, we noticed that cybersecurity became a popular thing for members of Congress to talk about, but it was difficult to trace some of their public statements back to actual spending.
What we couldn’t tell was whether the reasons we couldn’t identify programs based on their descriptions was because those programs were classified or because of a simple lack of clarity. (And if it was classification, we’d hope that policymakers wouldn’t be talking openly about those programs, of course).
We monitor and watchdog federal spending because we think it is important that taxpayers demand excellence from their government. In an era where we have competing demands of belt-tightening across government and increased calls for several types of security spending, cyber seemed like an area where a comprehensive review could help inform better policy decisions.
There’s also the fact that there is so much overlap and interplay between government interests and the private sector in cyber—private sector weaknesses can create problems so broad that they constitute personal and national security challenges.
Think about the Equifax breach, which creates potential threats by exposing the identities of 143 million people, not to mention the possible fraud against the Social Security Administration or the IRS. Or the hacking of Sony, where a foreign adversary went after a private company. The inability of government agencies to accurately describe their cyber investments and priorities hampers their ability to leverage private sector knowledge and resources, and vice versa.
What does the data show?
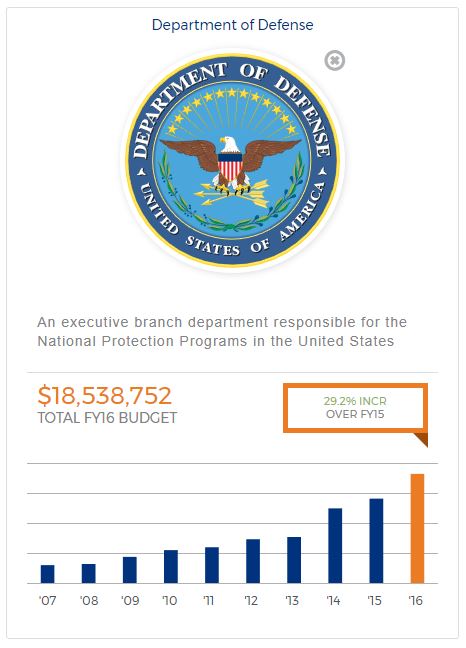
We learned as much from what is not in the data as what appears in the dataset. Unclassified spending is clearly just the tip of the iceberg when it comes to federal investments. Even in the unclassified setting, the Department of Defense accounts for the majority of cyber spending. In fiscal year 2016, 65% of cyber spending was in the Department of Defense, followed by the Department of the Treasury at 10% and the Department of Homeland Security at 6%.
There have been significant increases at Homeland Security—between fiscal years 2008 and 2016, unclassified cyber spending almost tripled. This makes sense given that Homeland Security is the main agency in securing all civilian computer systems, but the numbers don’t tell a complete story. Some increases are certainly the result of spending being recategorized as cyber as means to prioritize that item in a budget-constrained environment.
While it is not a surprise that Defense, Treasury, and Homeland Security are the leading agencies on cyber spending, there were some interesting findings on other agencies. For example, the National Science Foundation, a relatively small agency with a total fiscal year 2016 budget of $7.7 billion (as compared to the Department of Defense at $583 billion) is 4th in overall spending in real dollars.
What’s the most surprising finding?
The clearest finding is also the most surprising: No one person in the government would be able to answer the question of how much we spend on cyber across the government, and how we prioritize that spending.
The absence of a clear definition of “cyber” leave agencies without real guidance about not just how to code their spending—so that we can see whether it is cyber-related—but also how to invest those dollars.
That kind of high-level guidance needs to be set by Congress, and while there have been several laws and executive orders that relate to cyber spending in the last decade, none tackled the problem of providing a common set of terms, or a clear government-wide policy. And Congress itself recognizes the problem.
In fact, for fiscal year 2017 the Omnibus Appropriations bill said: “much of [cyber] funding is encompassed within larger programs and funding lines, which limits visibility and congressional oversight of requested funding for cyberspace activities specifically.” Congress went on to direct the Department of Defense Chief Information Officer to provide more detail on cyberspace activities.
The Bush administration developed a classified Comprehensive National Cybersecurity Initiative, and the Obama administration conducted a government wide review of cyber activities. But neither resulted in increased clarity at the legislative and budget level in the unclassified setting.
How do you hope the data is used?
We hope that this dataset will be used by researchers, journalists, policymakers, and chief information officers. We know the picture we’ve drawn doesn’t begin to capture the entire elephant, but it provides a starting point for researchers who have deep knowledge in a specific area. We created the database and display tool in a way that additional research findings can be added. There are many areas of further inquiry—the database does not identify contractors, for example, a level of detail which would certainly tell new stories.
As we have talked to staff on the Hill and colleagues at think tanks and other organizations, it is clear that looking at cyber spending across the government has raised new questions and framed new ideas for research—and ultimately, will support better policy recommendations.

 Mike Austin
Mike Austin

